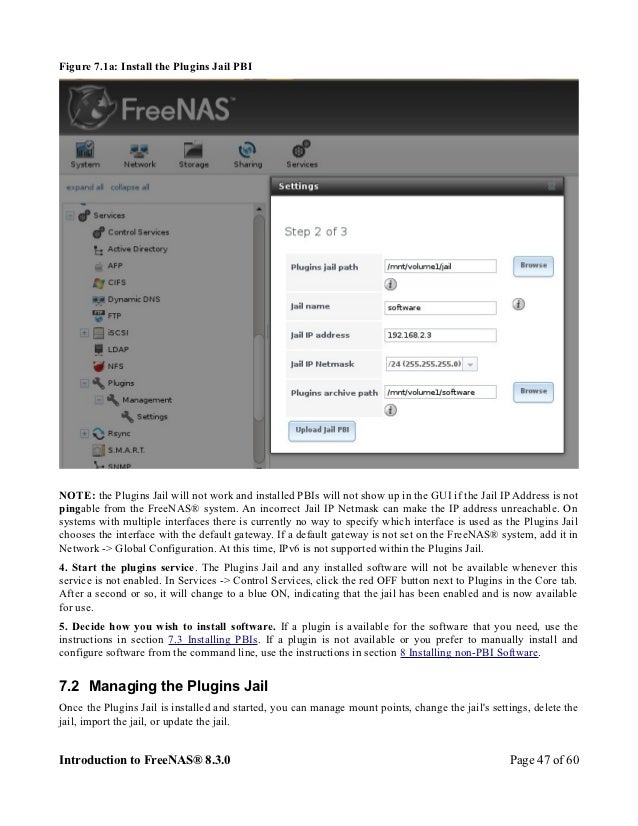
Freenas Full Install Xzxx
FreeNAS is an open source network-attached storage (NAS) operating system based on BSD and the ZFS filesystem with integrated RAID support. FreeNAS operating system is totally based on BSD and can be installed on virtual machines or in physical machines to share data storage via a computer network.
In previous articles we have shown how to set up a basic Hyper-V virtual machine that works with FreeBSD and FreeNAS as well as how to configure the Hyper-V VM and boot FreeNAS in it. The next step of course is to install FreeNAS to a vhd, so it no longer needs to run off of the LiveCD. This is primarily important so you can configure FreeNAS and save that configuration through reboots. Also, as FreeNAS seems to only work with drives attached to the IDE controllers, installing FreeNAS to a vhd allows one to free up one IDE channel for another drive (by removing the default DVD drive).
First off, as with any good article the test configuration. As a note from my previous experience running FreeNAS in Hyper-V, CPU utilization tends to be pretty low. The more memory you can give the VM the better (FreeNAS caches data in RAM). With all that said, multiple drives is a bit of a waste with FreeNAS since it does not seem to work with the default Hyper-V SCSI adapter. Here’s the configuration, and much more than you need to run Hyper-V Server R2 and FreeNAS:
- CPU: Intel Core i7 920
- Motherboard: Supermicro X8ST3-F
- Memory: Patriot Viper 12GB DDR3 1600
- Case (1): Norco RPC-4020
- Case (2): Norco RPC-4220
- Drives: Seagate 7200rpm 1.5TB, Hitachi 7200rpm 2TB and 1TB, Western Digital Green 1.5TB
- Controller: Areca ARC-1680LP
- SAS Expanders: 2x HP SAS Expander
- NIC (additional): Intel Pro/1000 PT Quad
- Host OS: Windows Server 2008 R2 with Hyper-V installed
For this guide I am assuming that you already have completed the previously linked steps and you have booted into a FreeNAS LiveCD environment. From here, we will install FreeNAS into a vhd so it can run off of a “disk” in Hyper-V. This guide will cover installing FreeNAS from a LiveCD boot to a local VHD installation in Hyper-V. At the conclusion, you will be in the FreeNAS administrative WebGUI.
First, with an already booted VM from Part 1, select option 9 and hit enter.
Second, I like to use option 3 here. Ideally, if FreeNAS worked with Hyper-V’s SCSI controller, we wouldn’t necessarily want to use option 1, however, since FreeNAS can only use Hyper-V IDE disks, you have to make the best of the disk you have. It should be noted, a 120GB SSD would be great here since it is under the IDE drive capacity limit, and would make a cool swapfile.
Third, click OK after minding the warnings that all partitions and data will be erased, assuming of course that you don’t have any data on the vhd.
Fourth, Hyper-V makes it easy to select the CD/ DVD drive for the installation media… there’s only one option here so click OK.
Fifth, install the FreeNAS OS to your Virtual HD (vhd). You will see in this example I’m using a 2GB drive. FreeNAS has a fairly small footprint.
Sixth, chose and OS partition size. The minimum is 128MB for FreeNAS. For the sake of the guide I just used the minimum but feel free to make it larger if you desire.
Next, (the seventh step in the guide) click yes to the swap partition.
Eighth, give the swap partition some disk space.
The next step I am combining a few to make everything easy. First, you need to eject the FreeNAS installation ISO from the Hyper-V Virtual Machine. Click on Media – > DVD Drive – Eject FreeNAS. It is highlighted in the screen shot below. Then hit Enter.
Tenth, assuming your Hyper-V VM does not actually reboot (mine doesn’t for some reason) you can use the Control Alt Delete (or Ctrl-Alt-Del if you prefer) button to restart the VM.
Now it is time to set up basic networking to get the FreeNAS VM operational. The next step is important since I have yet to see a FreeNAS Hyper-V VM networking work out of the box.
In your newly install VM, you should see a familiar menu. Select option 1, “Assign interfaces”. I am going to assume for the remainder of the guide that you are using FreeNAS with a DHCP server since this is only a quick start guide. To save bandwidth I am reusing the picture from Step 1.
You should see something similar to this screen next. I just hit OK.
Next, assuming you followed the previous guides so you only have one VM, click none Finish and exit configuration:
If you get another screen after hitting OK there, just say yes and you should be back at the main menu. Now select option 2 Set LAN IP Address:
For the purpose of this guide, we will be using DHCP so click Yes.
The next screen allows you to use IPv6. Enable if you want, but I am selecting No.
Ok, enough of the Hyper-V GUI. Time to login to FreeNAS’s WebGUI! If everything worked, you should be able to go to http://freenas/login.php
When your browser loads, you should now see the FreeNAS administrative WebGUI. Hello FreeNAS Part 2!
Congratulations, you now have FreeNAS working in Hyper-V! Next steps would be to add additional pass-through disks and then configure the virtual machine. If you were wondering, the FreeNAS default login is:
- Login name: admin
- Login password: freenas
Next up for Hyper-V installation guides will be OpenFiler. I will say, I’ve been playing quite a bit with OpenSolaris, and I have a few flavors “working” (as in they boot) in Hyper-V but none are ready for prime time at the moment. Hopefully one of these days, all of these OSes will come with compiled Hyper-V integration components, but alas, that’s another story altogether.
If there is anything I missed, feel free to leave a comment.
Hi.
I installed the FreeNAS on a hyper-v server, I set up a network for it.
But it cant find a DHCP and when i enter an IP manually it wont work on the network either (yes i use the correct range and mask).
When i boot a windows client on the same network interface that i use on the freeNAS, that client works with dynamic and static IP.
Any ide?
Bibi40k
FreeNAS Aware
i am new to this community and i decided to mix info from How to install OpenVPN inside a jail in FreeNAS 9.2.1.6+ with access to remote hosts via NAT and OpenVPN On FreeBSD 10.3 tutorials.
Please report inconsistency.
 change-log: 0.5 - 2018.10.14 - Added note that full restart is required sometimes
change-log: 0.5 - 2018.10.14 - Added note that full restart is required sometimes0.4 - 2018.07.26 - Removed 'comp-lzo' from configuration due to becoming obsolete
0.3 - 2018.02.18 - Minor touches and test everything from scratch following all the steps
0.2 - 2018.02.17 - Beautify code and few more details
0.1 - 2018.02.16 - First release
Legend:
- Green text - should remain like it is
- Blue text - you may cange it if you like
- Red text - needs to be changed by you
Requirements:
- FreeNAS 11.1-U1 ( may work with other versions either )
- FreeNAS User with ssh access and sudo
- SSH Client ( Putty for Windows and Terminal for MAC )
- Admin access to the router where FreeNAS exists
- Own domain or domain updated by DDNS or a static IP
- Please follow this step by step tutorial before ask for help
- Home Network: 192.168.1.0/24 ( LAN where is your FreeNAS )
- NAT Network: 10.8.0.0/24 ( virtual LAN between VPN clients and your LAN )
- Domain: nas.mydomain.com
- VPN Server Port: 1194 UDP
- VPN Outside Access Port: 443 UDP
- Certificate Authority Password: Password1
- Bibi40k Client Certificate Password: Password2
3,2,1.. START
Use FreeNAS Web GUI
Jails -> Add Jail ( Jail Name: OpenVPN, keep default settings )SSH to your FreeNAS box
Get everything updated and install necessary apps
Install Freenas 11 On Usb
Create directories for OpenVPN
Copy necessary files
Easy-RSA ( edit /usr/local/etc/openvpn/easy-rsa/vars )
set_var EASYRSA_REQ_PROVINCE 'California'
set_var EASYRSA_REQ_CITY 'San Francisco'
set_var EASYRSA_REQ_ORG 'Copyleft Certificate Co'
set_var EASYRSA_REQ_EMAIL 'me@mydomain.com'
set_var EASYRSA_REQ_OU 'My Organizational Unit'
# The default crypto mode is rsa; ec can enable elliptic curve support.
# Note that not all software supports ECC, so use care when enabling it.
# Choices for crypto alg are: (each in lower-case)
# * rsa
# * ec
#set_var EASYRSA_ALGO rsa
# Define the named curve, used in ec mode only:
#set_var EASYRSA_CURVE secp384r1
# In how many days should the root CA key expire?
set_var EASYRSA_CA_EXPIRE 3650
# In how many days should certificates expire?
set_var EASYRSA_CERT_EXPIRE 3650
echo 'You appear to be sourcing an Easy-RSA 'vars' file.' >&2
echo 'This is no longer necessary and is disallowed. See the section called' >&2
echo 'How to use this file' near the top comments for more details.' >&2
return 1
fi
set_var EASYRSA_REQ_COUNTRY 'US'
set_var EASYRSA_REQ_PROVINCE 'California'
set_var EASYRSA_REQ_CITY 'San Francisco'
set_var EASYRSA_REQ_ORG 'Copyleft Certificate Co'
set_var EASYRSA_REQ_EMAIL 'me@mydomain.com'
set_var EASYRSA_REQ_OU 'My Organizational Unit'
set_var EASYRSA_KEY_SIZE 2048
set_var EASYRSA_CA_EXPIRE 3650
set_var EASYRSA_CERT_EXPIRE 3650
Generate Keys
Build Certificate Authority ( follow instructions using Password1 and common name )
Build Server Certificates
Build Client Certificate ( use unique name for each certificate, use Bibi40k with Password2 and authorize with Password1 )
Generate Diffie Hellman Parameters ( /usr/local/etc/openvpn/easy-rsa/pki/dh.pem )
Generate the TA key
Copy Keys Together
OpenVPN ( edit /usr/local/etc/openvpn/openvpn.conf )
# OpenVPN can also use a PKCS #12 formatted key file
# (see 'pkcs12' directive in man page).
ca /usr/local/etc/openvpn/keys/ca.crt
cert /usr/local/etc/openvpn/keys/openvpn-server.crt
key /usr/local/etc/openvpn/keys/openvpn-server.key # This file should be kept secret
# Diffie hellman parameters.
# Generate your own with:
# openssl dhparam -out dh2048.pem 2048
dh /usr/local/etc/openvpn/keys/dh.pem
# to reach other private subnets behind
# the server. Remember that these
# private subnets will also need
# to know to route the OpenVPN client
# address pool (10.8.0.0/255.255.255.0)
# back to the OpenVPN server.
;push 'route 192.168.10.0 255.255.255.0'
push 'route 192.168.1.0 255.255.255.0'
# on the server and '1' on the clients.
tls-auth /usr/local/etc/openvpn/keys/ta.key 0 # This file is secret
remote-cert-tls client
# non-Windows systems.
user nobody
group nobody
proto udp
dev tun
ca /usr/local/etc/openvpn/keys/ca.crt
cert /usr/local/etc/openvpn/keys/openvpn-server.crt
key /usr/local/etc/openvpn/keys/openvpn-server.key # This file should be kept secret
dh /usr/local/etc/openvpn/keys/dh.pem
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push 'route 192.168.1.0 255.255.255.0'
keepalive 10 120
tls-auth /usr/local/etc/openvpn/keys/ta.key 0 # This file is secret
remote-cert-tls client
cipher AES-256-CBC
user nobody
group nobody
persist-key
persist-tun
status openvpn-status.log
verb 3
explicit-exit-notify 1
Client Config ( /usr/local/etc/openvpn/Bibi40k.conf )
# You can have multiple remote entries
# to load balance between the servers.
;remote my-server-1 1194
remote nas.mydomain.com443
# See the server config file for more
# description. It's best to use
# a separate .crt/.key file pair
# for each client. A single ca
# file can be used for all clients.
ca ca.crt
cert Bibi40k.crt
key Bibi40k.key
#dhcp-option DNS 192.168.1.1
#redirect-gateway def1
dev tun
proto udp
remote nas.mydomain.com443
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert Bibi40k.crt
key Bibi40k.key
remote-cert-tls server
tls-auth ta.key 1
cipher AES-256-CBC
# Act as Gateway: Uncomment only if you need this
#dhcp-option DNS 192.168.1.1
#redirect-gateway def1
verb 3
Server NAT Configuration ( create /usr/local/etc/ipfw.rules and add green text )
EPAIR=$(/sbin/ifconfig -l tr ' ' 'n' /usr/bin/grep epair)
ipfw -q -f flush
ipfw -q nat 1 config if ${EPAIR}
ipfw -q add nat 1 all from 10.8.0.0/24 to any out via ${EPAIR}
ipfw -q add nat 1 all from any to any in via ${EPAIR}
TUN=$(/sbin/ifconfig -l tr ' ' 'n' /usr/bin/grep tun)
ifconfig ${TUN} name tun0
openvpn_if='tun'
openvpn_configfile='/usr/local/etc/openvpn/openvpn.conf'
openvpn_dir='/usr/local/etc/openvpn/'
cloned_interfaces='tun'
gateway_enable='YES'
firewall_enable='YES'
firewall_script='/usr/local/etc/ipfw.rules'
*.* /var/log/ppp.log
!openvpn
*.* /var/log/openvpn.log
!*
/var/log/xferlog 600 7 100 * JC
/var/log/openvpn.log 600 30 * @T00 ZC
Jails -> Select OpenVPN Jail -> RestartNote: sometimes is necessary to restart whole FreeNAS server because the routes are build properly after full restart.
SSH to your FreeNAS box and make some checks
Let's send our OpenVPN client files and test connection from outside